Thẻ
How to secure your API gateway
In this blog, I will cover the 6 methods that technology leaders need to incorporate to secure and protect APIs.
Table of content
- Authentication
- Authorization
- Rate limiting
- CORS
- Encrypt Data Transmitted
- Validate requests and responses
- Conclusion
Authentication
- What is authentication? Authentication is the process of verifying users, services, or applications that are allowed or denied access to organization resources.
- Is it important? Authentication is important because it helps to protect your application with less risk.
- What are common methods? There are 6 common authentication methods: Username & Password, API Keys, Tokens, OTP, Certificates, and Biometrics.
- Username & Password: This is the common method that is often used on any application.
- Tokens: In the previous article, I already showed you how to verify and decode JWT from cognito with Node.js NODEJS VERIFY AND DECODE COGNITO JWT TOKENS.
- One-Time Password (OTP): We are using SMS messages to deliver code generated to you. You can follow in CREATE COGNITO USER POOL WITH AWS CDK.
Authorization
- What is authorization? Authorization is the process based on roles to limit users, services, and applications' ability to access your resources.
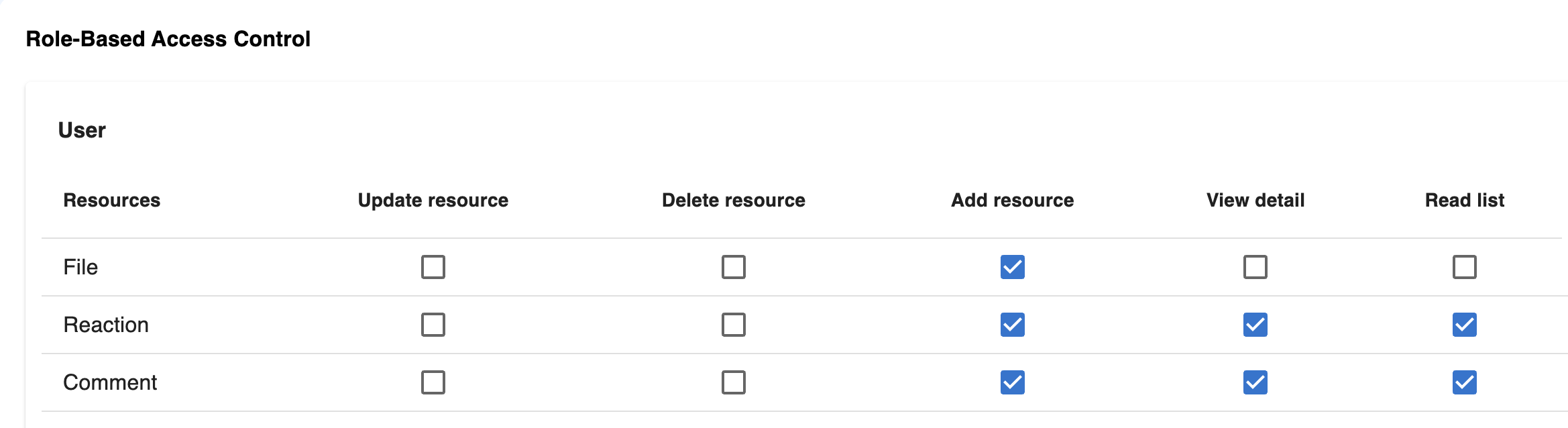
- How many authorization methods? Authorization can be expressed in various ways: Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), Rule-Based Access Control (RBAC), Discretionary Access Control (DAC), and Mandatory Access Control (MAC).
- Role-Based Access Control (RBAC): This is mentioned in the previous post 🚀 USING BITWISE OPERATORS TO BUILD A RBAC IN NODE.JS 🚀
 Rate Limiting
Rate Limiting
- What is the rate-limiting for? Using the rate limiting to determine the maximum number of requests allowed per client with a specific time window.
- For example, The HTTP Code response is 429 after login failed a lot of times.
CORS
- CORS stands for Cross-Origin Resource Sharing.
- It is a security feature implemented by web browsers to restrict web page scripts from making requests to a different domain than the one that served the web page.
- For example: Get an error response after having a request to the dinhthanhcong.info server with a different domain.
Encrypt Data Transmitted
- Enable HTTPS (HTTP Secure) for all incoming and outgoing traffic to encrypt data in transit and prevent eavesdropping, tampering, and man-in-the-middle attacks.
- Using TLS (Transport Layer Security) is a crucial step in encrypting data in transit between the client and the server. TLS provides secure communication between client and server over the internet and is a widely used protocol that has been extensively tested for security.
Validate requests and responses
- Input validation is the process of checking user input to ensure that it conforms to the expected format, type, length, and range of values.
- Validating requests and responses in an API is essential for ensuring data integrity, security, and adherence to the API's specifications.
- In previous articles: I introduced API SCHEMA VALIDATION
Conclusion
By implementing these security measures, you can strengthen the overall security posture of your API gateway, protect sensitive data, and mitigate the risk of security breaches and unauthorized access to your backend systems and services. With a proactive approach to security, you can build trust with your users and partners, and confidently deliver secure and reliable APIs.
Good luck to you, hope this post is of value to you!!!!